-
SWATCH2010 watch line color in summer in spring return
 Spring/summer SWATCH2010 watches Watch out when Giants classic interpretation ofSwatch this season returning to the source, to restart the brand DNA, the launch of the new NI Shang series. Not only colorful table 20, also includes the corresponding color Jewelry Accessories, select rich, the price is also very good.NI Shang series takes us back to the initial origin of Swatch-10 bright shiny standards-Gent watches, each matching shiny solid color plastic strap, as well as with color case and dial. Another 10 Watch Matt solid color plastic strap, plastic case with strap match, and White Dial with digital color markers and indices. Funny thing is, each color corresponds to a cocktail watches jewelry, make people feel good and refreshing cool summer State of mind.Swatch NI Shang series watches are a solid color, so easy to match, no matter the eye-catching embellishment is and dress color echo fashion attitude can show your unique personality.
Spring/summer SWATCH2010 watches Watch out when Giants classic interpretation ofSwatch this season returning to the source, to restart the brand DNA, the launch of the new NI Shang series. Not only colorful table 20, also includes the corresponding color Jewelry Accessories, select rich, the price is also very good.NI Shang series takes us back to the initial origin of Swatch-10 bright shiny standards-Gent watches, each matching shiny solid color plastic strap, as well as with color case and dial. Another 10 Watch Matt solid color plastic strap, plastic case with strap match, and White Dial with digital color markers and indices. Funny thing is, each color corresponds to a cocktail watches jewelry, make people feel good and refreshing cool summer State of mind.Swatch NI Shang series watches are a solid color, so easy to match, no matter the eye-catching embellishment is and dress color echo fashion attitude can show your unique personality.  Spring/summer SWATCH2010 watches
Spring/summer SWATCH2010 watches Spring/summer SWATCH2010 watches
Spring/summer SWATCH2010 watches Spring/summer SWATCH2010 watches
Spring/summer SWATCH2010 watches Spring/summer SWATCH2010 watches
Spring/summer SWATCH2010 watches Spring/summer SWATCH2010 watchesWatch collection spring/summer SWATCH2010. svbxs DL{margin:12px;min-height:336px} Watch out when Giants classic interpretation ofWatches swatch color color color in spring and summer jewelry accessory plastic
Spring/summer SWATCH2010 watchesWatch collection spring/summer SWATCH2010. svbxs DL{margin:12px;min-height:336px} Watch out when Giants classic interpretation ofWatches swatch color color color in spring and summer jewelry accessory plastic -
Fall/winter Hermes two new luxury watches
This "classic" watches exude such watch pure and elegant, designed by Henri d'Origny, is a tribute to the 19th century legendary three-masted ships. NIA calf table all the more simple Bar é bring out the silver Opal dial relief contours, in addition there is a self-winding mechanical functions.
 NIA calfskin strap with a silver BAR é CLIPPER Opal dial diameter of 39 mm watchesBAR Café NIA calfskin strap CLIPPER and Opal silver plated dial diameter of 39 mm watch. Movado series of three dedicated to the simplicityCLIPPER of the Tan colored dial and black rubber strap 44 mm diameter diving chronograph Movado series of three dedicated to the simplicityCLIPPER of the Tan colored dial and black rubber strap 44 mm diameter diving chronographAs the series fashion watch movement in the design of new products, watch highlights of campaign activity, and has a self-winding mechanical function. 44 mm diameter case entirely of titanium, which is lighter than steel made in sturdy metal often used in rowing. 200 m depth waterproof performance, coupled with a sporty rubber strap, this watch is definitely the best partner for water sports!.svbxs dl{margin:12px;min-height:336px}Fall/winter Hermes luxury watches watches dial Opal bracelet silver rubber
NIA calfskin strap with a silver BAR é CLIPPER Opal dial diameter of 39 mm watchesBAR Café NIA calfskin strap CLIPPER and Opal silver plated dial diameter of 39 mm watch. Movado series of three dedicated to the simplicityCLIPPER of the Tan colored dial and black rubber strap 44 mm diameter diving chronograph Movado series of three dedicated to the simplicityCLIPPER of the Tan colored dial and black rubber strap 44 mm diameter diving chronographAs the series fashion watch movement in the design of new products, watch highlights of campaign activity, and has a self-winding mechanical function. 44 mm diameter case entirely of titanium, which is lighter than steel made in sturdy metal often used in rowing. 200 m depth waterproof performance, coupled with a sporty rubber strap, this watch is definitely the best partner for water sports!.svbxs dl{margin:12px;min-height:336px}Fall/winter Hermes luxury watches watches dial Opal bracelet silver rubber -
Fall/winter Hermes two new luxury watches
This "classic" watches exude such watch pure and elegant, designed by Henri d'Origny, is a tribute to the 19th century legendary three-masted ships. NIA calf table all the more simple Bar é bring out the silver Opal dial relief contours, in addition there is a self-winding mechanical functions.
 NIA calfskin strap with a silver BAR é CLIPPER Opal dial diameter of 39 mm watchesBAR Café NIA calfskin strap CLIPPER and Opal silver plated dial diameter of 39 mm watch. Movado series of three dedicated to the simplicityCLIPPER of the Tan colored dial and black rubber strap 44 mm diameter diving chronograph Movado series of three dedicated to the simplicityCLIPPER of the Tan colored dial and black rubber strap 44 mm diameter diving chronographAs the series fashion watch movement in the design of new products, watch highlights of campaign activity, and has a self-winding mechanical function. 44 mm diameter case entirely of titanium, which is lighter than steel made in sturdy metal often used in rowing. 200 m depth waterproof performance, coupled with a sporty rubber strap, this watch is definitely the best partner for water sports!.svbxs dl{margin:12px;min-height:336px}Fall/winter Hermes luxury watches watches dial Opal bracelet silver rubber
NIA calfskin strap with a silver BAR é CLIPPER Opal dial diameter of 39 mm watchesBAR Café NIA calfskin strap CLIPPER and Opal silver plated dial diameter of 39 mm watch. Movado series of three dedicated to the simplicityCLIPPER of the Tan colored dial and black rubber strap 44 mm diameter diving chronograph Movado series of three dedicated to the simplicityCLIPPER of the Tan colored dial and black rubber strap 44 mm diameter diving chronographAs the series fashion watch movement in the design of new products, watch highlights of campaign activity, and has a self-winding mechanical function. 44 mm diameter case entirely of titanium, which is lighter than steel made in sturdy metal often used in rowing. 200 m depth waterproof performance, coupled with a sporty rubber strap, this watch is definitely the best partner for water sports!.svbxs dl{margin:12px;min-height:336px}Fall/winter Hermes luxury watches watches dial Opal bracelet silver rubber -
Flashy beauty of alienation recommended specification pointer watches
As history most long of wrist table style one of, specification pointer wrist table not only is "retro breath" most rich of wrist table style, and spread has, it of process and styling are show has alienation today of glitz of beauty, regardless of market Shang of modern style how range, it on in there retained live most original and pure of gentleman attitude, slowly to tells time of beauty. 4 specification pointer watches, let you enjoy the bustling behind the elegant appeal.
 LeCoultre Master Grande Tradition standard pointers Minute RepeaterLeCoultre Master Grande Tradition standard pointers Minute Repeater Master series will gauge pointer and combining three functions, showing pure elegant Master Grande Tradition standard pointers Minute Repeater. Texture and pattern on the dial, with each other on the dial pointer to the Golden echoes, radian on the dial and white, showing volume refined layout. In addition, the mechanical watch is powered by a type 947 movement, combines three functions and standard indicators, with a two-week power reserve. Two major pointer on the dial in a different axis to ensure display of accurate and easier minute read. The system can be made at different times to instruct noninterference in each draw their own running track, and put an end to all possibility of friction and contact, friction and contact may affect potential obstacles to watch good mechanical operation. It can be said that standard time display remains an exclusively ultra precision complex functions of a watch. Second disc on both sides is the mainspring torque measurement display (left) and power reserve indication (right). An ear, not forgetting the sweet sound is also a highlight of it.Series: LeCoultre Master Grande Tradition seriesMovement: mechanical movement 947R calibrePower reserve: two weeksLimited Edition: 100 piecesFeatures: three questions, standard pointer
LeCoultre Master Grande Tradition standard pointers Minute RepeaterLeCoultre Master Grande Tradition standard pointers Minute Repeater Master series will gauge pointer and combining three functions, showing pure elegant Master Grande Tradition standard pointers Minute Repeater. Texture and pattern on the dial, with each other on the dial pointer to the Golden echoes, radian on the dial and white, showing volume refined layout. In addition, the mechanical watch is powered by a type 947 movement, combines three functions and standard indicators, with a two-week power reserve. Two major pointer on the dial in a different axis to ensure display of accurate and easier minute read. The system can be made at different times to instruct noninterference in each draw their own running track, and put an end to all possibility of friction and contact, friction and contact may affect potential obstacles to watch good mechanical operation. It can be said that standard time display remains an exclusively ultra precision complex functions of a watch. Second disc on both sides is the mainspring torque measurement display (left) and power reserve indication (right). An ear, not forgetting the sweet sound is also a highlight of it.Series: LeCoultre Master Grande Tradition seriesMovement: mechanical movement 947R calibrePower reserve: two weeksLimited Edition: 100 piecesFeatures: three questions, standard pointer LeCoultre Master Grande Tradition standard pointers Minute RepeaterLeCoultre Master Grande Tradition standard pointers Minute Repeater
LeCoultre Master Grande Tradition standard pointers Minute RepeaterLeCoultre Master Grande Tradition standard pointers Minute Repeater Universal Portugal IW544401 man mechanical movement watch Vacheron Constantin salute Oriental lacquerUniversal Portugal IW544401 man mechanical movement watchUniversal Portugal family specification pointer watches, three-pin design with case diameter 43 mm integration even more low-key than black on dark grey dial, narrow pointers such as a touch of silver secretly transferred. Orbit minute and vortex pattern in the two smaller dials the dial's sharp white, retro decorating minimalist elegance. 98245 manually wound mechanical pocket watch movement as metaphor in Schaffhausen tradition and pride, and uncompromising attention to detail of 3/4 nickel silver alloy splint Ambilight is through the surface at a glance.Series: Portugal series, men's watchMovement: mechanical movement, model number: Cal.98245Case: stainless steelSize: 43.1mmGlass: Sapphire CrystalBracelet/strap: alligator leatherWater resistant: 30 m
Universal Portugal IW544401 man mechanical movement watch Vacheron Constantin salute Oriental lacquerUniversal Portugal IW544401 man mechanical movement watchUniversal Portugal family specification pointer watches, three-pin design with case diameter 43 mm integration even more low-key than black on dark grey dial, narrow pointers such as a touch of silver secretly transferred. Orbit minute and vortex pattern in the two smaller dials the dial's sharp white, retro decorating minimalist elegance. 98245 manually wound mechanical pocket watch movement as metaphor in Schaffhausen tradition and pride, and uncompromising attention to detail of 3/4 nickel silver alloy splint Ambilight is through the surface at a glance.Series: Portugal series, men's watchMovement: mechanical movement, model number: Cal.98245Case: stainless steelSize: 43.1mmGlass: Sapphire CrystalBracelet/strap: alligator leatherWater resistant: 30 m Universal Portugal IW544401 man mechanical movement watchUniversal Portugal IW544401 man mechanical movement watch
Universal Portugal IW544401 man mechanical movement watchUniversal Portugal IW544401 man mechanical movement watch Glashutte Original Senator Senate specification pointer watchesGlashutte Original Senator Senate specification pointer watches This elegant watch is loaded in 42 mm polished red gold or Platinum case, dial position, by special arrangement, and shrink to fit your wrist size. Dial is divided into four regions, namely specification pointer and a power reserve display. Specification pointer design configuration is very eye-catching, blue pointer is reflected in an eye-catching white chassis. Silver-coated lacquer Frost pattern dial with central location, being occupied with blued steel hands and their Polish roots, minute, above and below, respectively, smaller clock display and small seconds disc. The ring around the circumference of the dial is finely portrayed, by carving and plating added black, hours on the dial and Roman numerals is also portrayed in the same way. Glashutte Original iconic large Calendar window is positioned at the 3 o'clock position, black number being printed on ivory dish, fit seamlessly into the overall design of the dial. Power-reserve indication is placed in the 9 position dial, the overall layout of harmony. On the dynamic, Glashutte Original Senator Chronometer Regulator based on the homemade hand-wound movement 58-01 58-04-driven movement, movement for minutes and seconds to accurately. Used second hand return to zero of the new devices allow the wearer to make it easier to adjust the correct time. Projection design, art appreciation, and more, this watch the previous steps.
Glashutte Original Senator Senate specification pointer watchesGlashutte Original Senator Senate specification pointer watches This elegant watch is loaded in 42 mm polished red gold or Platinum case, dial position, by special arrangement, and shrink to fit your wrist size. Dial is divided into four regions, namely specification pointer and a power reserve display. Specification pointer design configuration is very eye-catching, blue pointer is reflected in an eye-catching white chassis. Silver-coated lacquer Frost pattern dial with central location, being occupied with blued steel hands and their Polish roots, minute, above and below, respectively, smaller clock display and small seconds disc. The ring around the circumference of the dial is finely portrayed, by carving and plating added black, hours on the dial and Roman numerals is also portrayed in the same way. Glashutte Original iconic large Calendar window is positioned at the 3 o'clock position, black number being printed on ivory dish, fit seamlessly into the overall design of the dial. Power-reserve indication is placed in the 9 position dial, the overall layout of harmony. On the dynamic, Glashutte Original Senator Chronometer Regulator based on the homemade hand-wound movement 58-01 58-04-driven movement, movement for minutes and seconds to accurately. Used second hand return to zero of the new devices allow the wearer to make it easier to adjust the correct time. Projection design, art appreciation, and more, this watch the previous steps. Glashutte Original Senator Senate specification pointer watchesGlashutte Original Senator Senate specification pointer watches
Glashutte Original Senator Senate specification pointer watchesGlashutte Original Senator Senate specification pointer watches Piaget Emperador coussin regulator watchPiaget Emperador coussin regulator large style watch Earl retrograde feature combine with standard pointer of dial layout, create the Piaget Emperador coussin regulator wristwatch. Watches of rectangular dial of 12 points bit and 6 points bit the has a fan regional, 12 points bit of inverse jumped pointer from 0 seconds go to 30 seconds Hou, immediately jumped back 0 seconds, 6 points bit of pointer is received down from 30 seconds go to 60 seconds, jumped back 30 seconds, then again round to 12 points bit of pointer walking, reflected out of clever of idea, exquisite of process, was had to afforded modern watches art of diversity.Dial: BlueCase: 18K rose goldMovement: mechanical, Earl 835P manual windingFunctions: hour and minute time scale, Flyback second hand located at the 12 o'clock position, hour display at 6 o'clock position, Central minute hands displayPiaget Emperador coussin regulator watch Vacheron Constantin salute Oriental lacquerPiaget Emperador coussin regulator large style watch.svbxs dl{margin:12px;min-height:336px}Pointer watch dial movement count Jaeger LeCoultre series mechanical watch recommended
Piaget Emperador coussin regulator watchPiaget Emperador coussin regulator large style watch Earl retrograde feature combine with standard pointer of dial layout, create the Piaget Emperador coussin regulator wristwatch. Watches of rectangular dial of 12 points bit and 6 points bit the has a fan regional, 12 points bit of inverse jumped pointer from 0 seconds go to 30 seconds Hou, immediately jumped back 0 seconds, 6 points bit of pointer is received down from 30 seconds go to 60 seconds, jumped back 30 seconds, then again round to 12 points bit of pointer walking, reflected out of clever of idea, exquisite of process, was had to afforded modern watches art of diversity.Dial: BlueCase: 18K rose goldMovement: mechanical, Earl 835P manual windingFunctions: hour and minute time scale, Flyback second hand located at the 12 o'clock position, hour display at 6 o'clock position, Central minute hands displayPiaget Emperador coussin regulator watch Vacheron Constantin salute Oriental lacquerPiaget Emperador coussin regulator large style watch.svbxs dl{margin:12px;min-height:336px}Pointer watch dial movement count Jaeger LeCoultre series mechanical watch recommended -
Celebrities Clayton time series remodeling inspiration charm
Celebrities new Clayton wrist table series designed for city men design, lineage has brand by unique of derived from United States Han Burton of "beach life" breath, regardless of is 18K red gold manual Shang chain wrist table (Clayton 1830) or two paragraph 41 mm automatically Shang chain wrist table (Clayton 10052 and 10053), and spirit NI series 27 mm mechanical wrist table new (spirit NI 10113 and 10114), are will noble temperament and classic eternal thaw for one.
 Clayton, 1830 These watches cool knowledge can give you socksRed Gold sculpted 42 mm watches – Clayton, 1830This diameter 42 mm Watch Red Gold 18K sculpted, called Clayton, representatives for the series. The table is compact and delicate, reserves committed to the heritage of traditional crafts of a watchmaker's efforts, while meeting the highest standards of modern technology. Case with fine polished satin polished, to witness the excellence process. To meet the contours of the curved Sapphire Crystal mirror, which also uses the arc-shaped design of the dial, and acrylic resin glass mirror similar uses in the past.Uncompromising attention to detail of the dialThrough the arc of the watch dial white silver process, matching each of the figures and tables are placed in the appropriate location, and riveted to the bottom surface of the dial, 6 o a small seconds disc.Custom-made for celebrities of the movementThe table exquisitely and pure simplicity, carrying La Joux-Perret factory built specially for the famous movement of the movement (the number is 7381), when the barrel was full after the chain, it can provide 90 hours of power reserve watches. This superior movement through the transparent case back below, its eternal timeless qualities after years of baptism. Each movement have been carefully optimized, its rotor vibration frequency up to 21,600 times per hour. This high performance lens paired with famous Chronograph, watch artist's masterpiece, which complement the special movements of details is enough to make the wearer proud. Table decoration decorated bridge Geneva, round bottom plate decoration and elegant blued steel screws, through the transparent case back Sapphire Crystal glass are clearly visible. This new table 18K red gold case, with 50 m water resistant, set a very high level of technology in one.Clayton series time charm
Clayton, 1830 These watches cool knowledge can give you socksRed Gold sculpted 42 mm watches – Clayton, 1830This diameter 42 mm Watch Red Gold 18K sculpted, called Clayton, representatives for the series. The table is compact and delicate, reserves committed to the heritage of traditional crafts of a watchmaker's efforts, while meeting the highest standards of modern technology. Case with fine polished satin polished, to witness the excellence process. To meet the contours of the curved Sapphire Crystal mirror, which also uses the arc-shaped design of the dial, and acrylic resin glass mirror similar uses in the past.Uncompromising attention to detail of the dialThrough the arc of the watch dial white silver process, matching each of the figures and tables are placed in the appropriate location, and riveted to the bottom surface of the dial, 6 o a small seconds disc.Custom-made for celebrities of the movementThe table exquisitely and pure simplicity, carrying La Joux-Perret factory built specially for the famous movement of the movement (the number is 7381), when the barrel was full after the chain, it can provide 90 hours of power reserve watches. This superior movement through the transparent case back below, its eternal timeless qualities after years of baptism. Each movement have been carefully optimized, its rotor vibration frequency up to 21,600 times per hour. This high performance lens paired with famous Chronograph, watch artist's masterpiece, which complement the special movements of details is enough to make the wearer proud. Table decoration decorated bridge Geneva, round bottom plate decoration and elegant blued steel screws, through the transparent case back Sapphire Crystal glass are clearly visible. This new table 18K red gold case, with 50 m water resistant, set a very high level of technology in one.Clayton series time charm Clayton 10052 and 10053 These watches cool knowledge can give you socksClayton series automatic movement watches displayed hours, minutes, small seconds function, silver-plated dial (10052)This series Clayton fashion with a diameter of 41 mm, shape has a traditional sense of beauty, inspired by the famous 1950 launch of classic watches, value constant. Watch match round stainless-steel shell and elaborate curved lugs, perfect fit wrist. The rapid consumption of modern life, only the pursuit of timeless design, would make buying watches a real investment. The chronograph black alligator leather strap with a triple fold safety clasp of the iteration. Matching Silver Dial Arabic numerals and tables, designed to reproduce the history table features and traditional style. This balanced perfect watch has a retro aesthetic, water-resistant to 50 m, blue steel pointer to set off the beauty of the watch, youzhenpin is 4 Hz automatic winding mechanical movement driven. Through the Sapphire-Crystal back you can decorate it with spiral-shaped decoration at Geneva of rotor in a glance. Special design, show leadership, commitment and dedication of the young elite.Clayton series automatic movement watches displayed hours, minutes, small seconds function, black dial (10053)Professionals think, black dial gives watches decisive temperament, which is used in military field watches most of the color, the pointer on the dial more clear and easier to read. This series Clayton was the black dial, perfect expression of what's distinctive image, emphasizing the watch "strong bold" personality, to foil male masculine cities active in the workplace, smart revealed their aggressive demeanor. Watch steel case diameter 41 mm, Brown crocodile leather strap, dial with hours, minutes, display, small seconds at 6 locations, date display at the 3 position, equipped with Switzerland made self-winding mechanical movement, rotor and other parts have been carefully processed, highlighting the beauty of understated luxury, clear through the Sapphire Crystal case back watch.Ling NI 10113 and 10114In making bold use of ladies ' watches self-winding mechanical movement, not only can watch from the erosion of time, can also make the practical decorations remain alive. Wonderful mechanical movement is the core component of this table, through the transparent case back can appreciate its subtle operation. Famous watchmaking craftsmen, under the clock master and creative designers have always wanted to create an unsurpassed clock works. Now they can finally ladies ' watch the birth of pride long, people thought that only men would wear a mechanical movement watch, however, this watch is equipped with a high-precision mechanical movement designed for ladies.Transparent case back makes automatic movements are clearly visible, this classical spectrum immortal legends, its stainless-steel or pink gold ring engraved with a unique, eye-catching table, while the automatic movement is driving what's running through the surface of the transparent design is able to appreciate the quality of movement. This extremely smart design, will not only attract stylish women who are energetic, but also traditional ladies in nostalgic ecstasy, they focus on jewelry what's life and the movement of the style known as a durable, just ensure that it can be passed down through generations, forever long. Sophisticated series neon to the spirit of the stainless-steel or two-tone bracelet becomes the focus of attention. A cleverly designed bracelet wearing more comfortable futie, does not preclude a variety of movements. Ling NI series can also free replacement strap for each owner, and it not only suitable for everyday wear, you can meet the diverse needs of different occasions.Replaceable strapsIn order to meet these needs, celebrities have developed a patented strap, the strap can be easily disassembled without tools. Meanwhile, the brand also designed a series of leather or of satin for replaceable strap material, and provide a variety of color choices, for those who like to use accessories to charm women, the originality of the watch just can meet their needs. This delightful ingenuity, the wearer is also close to the fashion changes, changes in popular and the alternation of the seasons. Both equipped with high quality steel or two-tone bracelet neon watches new spirit, with Switzerland-made automatic movement and have seconds, its mother of Pearl Dial with 11 diamond, 6 position the dial also has a simple date. The two new tables so that women who wear them to show mature, independent of the true self..svbxs dl{margin:12px;min-height:336px}Kelidunkelidun series wristwatch movement celebrities dial design charms
Clayton 10052 and 10053 These watches cool knowledge can give you socksClayton series automatic movement watches displayed hours, minutes, small seconds function, silver-plated dial (10052)This series Clayton fashion with a diameter of 41 mm, shape has a traditional sense of beauty, inspired by the famous 1950 launch of classic watches, value constant. Watch match round stainless-steel shell and elaborate curved lugs, perfect fit wrist. The rapid consumption of modern life, only the pursuit of timeless design, would make buying watches a real investment. The chronograph black alligator leather strap with a triple fold safety clasp of the iteration. Matching Silver Dial Arabic numerals and tables, designed to reproduce the history table features and traditional style. This balanced perfect watch has a retro aesthetic, water-resistant to 50 m, blue steel pointer to set off the beauty of the watch, youzhenpin is 4 Hz automatic winding mechanical movement driven. Through the Sapphire-Crystal back you can decorate it with spiral-shaped decoration at Geneva of rotor in a glance. Special design, show leadership, commitment and dedication of the young elite.Clayton series automatic movement watches displayed hours, minutes, small seconds function, black dial (10053)Professionals think, black dial gives watches decisive temperament, which is used in military field watches most of the color, the pointer on the dial more clear and easier to read. This series Clayton was the black dial, perfect expression of what's distinctive image, emphasizing the watch "strong bold" personality, to foil male masculine cities active in the workplace, smart revealed their aggressive demeanor. Watch steel case diameter 41 mm, Brown crocodile leather strap, dial with hours, minutes, display, small seconds at 6 locations, date display at the 3 position, equipped with Switzerland made self-winding mechanical movement, rotor and other parts have been carefully processed, highlighting the beauty of understated luxury, clear through the Sapphire Crystal case back watch.Ling NI 10113 and 10114In making bold use of ladies ' watches self-winding mechanical movement, not only can watch from the erosion of time, can also make the practical decorations remain alive. Wonderful mechanical movement is the core component of this table, through the transparent case back can appreciate its subtle operation. Famous watchmaking craftsmen, under the clock master and creative designers have always wanted to create an unsurpassed clock works. Now they can finally ladies ' watch the birth of pride long, people thought that only men would wear a mechanical movement watch, however, this watch is equipped with a high-precision mechanical movement designed for ladies.Transparent case back makes automatic movements are clearly visible, this classical spectrum immortal legends, its stainless-steel or pink gold ring engraved with a unique, eye-catching table, while the automatic movement is driving what's running through the surface of the transparent design is able to appreciate the quality of movement. This extremely smart design, will not only attract stylish women who are energetic, but also traditional ladies in nostalgic ecstasy, they focus on jewelry what's life and the movement of the style known as a durable, just ensure that it can be passed down through generations, forever long. Sophisticated series neon to the spirit of the stainless-steel or two-tone bracelet becomes the focus of attention. A cleverly designed bracelet wearing more comfortable futie, does not preclude a variety of movements. Ling NI series can also free replacement strap for each owner, and it not only suitable for everyday wear, you can meet the diverse needs of different occasions.Replaceable strapsIn order to meet these needs, celebrities have developed a patented strap, the strap can be easily disassembled without tools. Meanwhile, the brand also designed a series of leather or of satin for replaceable strap material, and provide a variety of color choices, for those who like to use accessories to charm women, the originality of the watch just can meet their needs. This delightful ingenuity, the wearer is also close to the fashion changes, changes in popular and the alternation of the seasons. Both equipped with high quality steel or two-tone bracelet neon watches new spirit, with Switzerland-made automatic movement and have seconds, its mother of Pearl Dial with 11 diamond, 6 position the dial also has a simple date. The two new tables so that women who wear them to show mature, independent of the true self..svbxs dl{margin:12px;min-height:336px}Kelidunkelidun series wristwatch movement celebrities dial design charms -
Suede items so beautiful I want to wear
Suede wind full of cool chic flavor, is an annual fashion essential in the audience will choose to wear a single product, still no exception this year. Other than the classic camel, suede much more to buy a new-style this year, including Fuchsia suede items, and cast stone Blue Suede skirt. Suede were so beautiful, simply wanted to wear every day!

 ASOS items this year on a pink suede coat, if compared to the classic camel, pink to let you more?
ASOS items this year on a pink suede coat, if compared to the classic camel, pink to let you more? Or a pair of pink suede booties, let you fall and winter is no longer dark, a bit more gentle feeling.
Or a pair of pink suede booties, let you fall and winter is no longer dark, a bit more gentle feeling. Grey-blue suede jacket, inside take a wine-red long coat, the two colors mix together, make you feel amazing? And the grey-Blue Suede is really special.
Grey-blue suede jacket, inside take a wine-red long coat, the two colors mix together, make you feel amazing? And the grey-Blue Suede is really special. Deeper than the grey-blue is the closest of cast stone and Blue Suede, paired with a white shirt, sharp tonal contrast! This low profile and have a sense of color, you don't get to learn what?
Deeper than the grey-blue is the closest of cast stone and Blue Suede, paired with a white shirt, sharp tonal contrast! This low profile and have a sense of color, you don't get to learn what?
 Olive green suede coat, slightly darker in color, but olive is one of the fashionable hues in autumn and winter this year, coupled with the texture of Suede, olive becomes thicker feeling full.
Olive green suede coat, slightly darker in color, but olive is one of the fashionable hues in autumn and winter this year, coupled with the texture of Suede, olive becomes thicker feeling full. Suede skirt, paired with a white Tee, jacket casually donned long coats coats or denim jacket is thick, beautiful and decent and generous!
Suede skirt, paired with a white Tee, jacket casually donned long coats coats or denim jacket is thick, beautiful and decent and generous! Choosing a bit oversize style suede leather jacket did you try, if you haven't tried to see the renderings also want to try one?Suede pants, a driving factor is a bit difficult, but choosing a nine-minute length, agile and capable.Brick-red suede long trench coat and gas fields not only stronger, and suede leather coat to keep warm is better.Suede heels, than ordinary leather, more elegant, and honestly, I didn't start with the suede heels, but the closest Street to see more bloggers are choosing suede heels, eh.Boots can also consider starting with knee-length is also partly to keep warm, with a skirt or dress is OK.Design loose this long suede coat, worn on the body is full of texture, texture and suede leather bag in hand there are echoes.If you can't handle suede pants with wide legs, in fact, this nine-minute length of the trumpet can definitely give it a try, because simple slim design makes the overall mix is the atmosphere.Button suede skirt, matching a high-neck knit sweater, vintage and French literature.How can you forget this suede leather handbag bag, give you the match itself an accessory items.Suede dress with white sneakers, is there a feeling of retro taste mix and match highlights?Only suede detail suede jacket paired with a small bag, cute, with a sense of natural elegance.Well, these suede match, I hope you quickly took the book down! Que Gazelle three hundred flower facial mask natural.svbxs dl{margin:12px;min-height:336px} Que Gazelle three hundred flower facial mask naturalSuede mix coat items every blue jacket dresses cherry blossom
Choosing a bit oversize style suede leather jacket did you try, if you haven't tried to see the renderings also want to try one?Suede pants, a driving factor is a bit difficult, but choosing a nine-minute length, agile and capable.Brick-red suede long trench coat and gas fields not only stronger, and suede leather coat to keep warm is better.Suede heels, than ordinary leather, more elegant, and honestly, I didn't start with the suede heels, but the closest Street to see more bloggers are choosing suede heels, eh.Boots can also consider starting with knee-length is also partly to keep warm, with a skirt or dress is OK.Design loose this long suede coat, worn on the body is full of texture, texture and suede leather bag in hand there are echoes.If you can't handle suede pants with wide legs, in fact, this nine-minute length of the trumpet can definitely give it a try, because simple slim design makes the overall mix is the atmosphere.Button suede skirt, matching a high-neck knit sweater, vintage and French literature.How can you forget this suede leather handbag bag, give you the match itself an accessory items.Suede dress with white sneakers, is there a feeling of retro taste mix and match highlights?Only suede detail suede jacket paired with a small bag, cute, with a sense of natural elegance.Well, these suede match, I hope you quickly took the book down! Que Gazelle three hundred flower facial mask natural.svbxs dl{margin:12px;min-height:336px} Que Gazelle three hundred flower facial mask naturalSuede mix coat items every blue jacket dresses cherry blossom -
New blog watch CALIBRE DE Cartier Cartier card calendar series
On September 17, the World Watches Cartier top new Baroque fashion landmarks in Shanghai Bund origin "key set" private party space, offer Yao works to charm men in town–Bo Watches Cartier card calendar series (). Carry Cartier first-made self-winding mechanical movement, card calendar blog Watch series of high-end technology and designed to reach a large, known as another sincere breakthrough on the history of Cartier in watchmaking. The same day, Cartier's "core" party into a world full of stylish men, attracting men gathered in one of the elite from all walks. Zeng fanzhi, Qu Guangci, to Beijing, Yuan Yue, Ji Cheng, social heroes come; Tony Leung, Jonathan Lee, and Chang Chen-yueh, and Ethan, and Su, and Godfrey, fan of superstar celebrities such as striving to participate in more "core" party more star-studded.
 Mr Tony Leung Chiu-Wai and Cartier's Chief Executive Officer in the far East with Mr Lu Huiquan embed a large Roman numeral XII dialOn September 17, the World Watches Cartier top new Baroque fashion landmarks in Shanghai Bund origin "key set" private party space, offer Yao works to charm men in town–Bo Watches Cartier card calendar series. Carry Cartier first-made self-winding mechanical movement, card calendar blog Watch series of high-end technology and designed to reach a large, known as another sincere breakthrough on the history of Cartier in watchmaking. The same day, Cartier's "core" party into a world full of stylish men, attracting men gathered in one of the elite from all walks. Zeng fanzhi, Qu Guangci, to Beijing, Yuan Yue, Ji Cheng, social heroes come; Tony Leung, Jonathan Lee, and Chang Chen-yueh, and Ethan, and Su, and Godfrey, fan of superstar celebrities such as striving to participate in more "core" party more star-studded.
Mr Tony Leung Chiu-Wai and Cartier's Chief Executive Officer in the far East with Mr Lu Huiquan embed a large Roman numeral XII dialOn September 17, the World Watches Cartier top new Baroque fashion landmarks in Shanghai Bund origin "key set" private party space, offer Yao works to charm men in town–Bo Watches Cartier card calendar series. Carry Cartier first-made self-winding mechanical movement, card calendar blog Watch series of high-end technology and designed to reach a large, known as another sincere breakthrough on the history of Cartier in watchmaking. The same day, Cartier's "core" party into a world full of stylish men, attracting men gathered in one of the elite from all walks. Zeng fanzhi, Qu Guangci, to Beijing, Yuan Yue, Ji Cheng, social heroes come; Tony Leung, Jonathan Lee, and Chang Chen-yueh, and Ethan, and Su, and Godfrey, fan of superstar celebrities such as striving to participate in more "core" party more star-studded. International superstar Tony Leung Chiu-Wai to visit the Cartier Conference site
International superstar Tony Leung Chiu-Wai to visit the Cartier Conference site Music Godfather got wit the words and music for guests riveting performance
Music Godfather got wit the words and music for guests riveting performance Popular Idol Ethan
Popular Idol Ethan Popular Idol EthanThe day of the event, Locke Bund origin on flat ground a lavish Cartier and "Palace of time" gingerly "through" infrared clouds of the mysterious corridor, and then "broke into" complex insurance, can be in the home is surrounded by a 360 ° image of the party. Passion and dynamics of light flowing freely in the walls: the exquisite detail of the movement, dial contours appear solid, super unique Roman conversion of time scale. Party climax, Cartier far East together at Mr Tony Leung Chiu-Wai Mr Lu Huiquan, Chief Executive, will be huge when you embed dial Roman numeral XII, reached a boiling point.
Popular Idol EthanThe day of the event, Locke Bund origin on flat ground a lavish Cartier and "Palace of time" gingerly "through" infrared clouds of the mysterious corridor, and then "broke into" complex insurance, can be in the home is surrounded by a 360 ° image of the party. Passion and dynamics of light flowing freely in the walls: the exquisite detail of the movement, dial contours appear solid, super unique Roman conversion of time scale. Party climax, Cartier far East together at Mr Tony Leung Chiu-Wai Mr Lu Huiquan, Chief Executive, will be huge when you embed dial Roman numeral XII, reached a boiling point. Passion party home surrounded by 360 ° images and dynamic card calendar blog watch shadows on the walls free flowing
Passion party home surrounded by 360 ° images and dynamic card calendar blog watch shadows on the walls free flowing Tony Leung Chiu-Wai affectionate interpretation Cartier charm manBlog Watch Cartier card calendar series. svbxs DL{margin:12px;min-height:336px} Watch how could you not know Blancpain 50 fathomsLeung Cartier Cartier watches party Ethan Chang Chen-yueh, men Watch how could you not know Blancpain 50 fathoms
Tony Leung Chiu-Wai affectionate interpretation Cartier charm manBlog Watch Cartier card calendar series. svbxs DL{margin:12px;min-height:336px} Watch how could you not know Blancpain 50 fathomsLeung Cartier Cartier watches party Ethan Chang Chen-yueh, men Watch how could you not know Blancpain 50 fathoms -
New blog watch CALIBRE DE Cartier Cartier card calendar series
On September 17, the World Watches Cartier top new Baroque fashion landmarks in Shanghai Bund origin "key set" private party space, offer Yao works to charm men in town–Bo Watches Cartier card calendar series (). Carry Cartier first-made self-winding mechanical movement, card calendar blog Watch series of high-end technology and designed to reach a large, known as another sincere breakthrough on the history of Cartier in watchmaking. The same day, Cartier's "core" party into a world full of stylish men, attracting men gathered in one of the elite from all walks. Zeng fanzhi, Qu Guangci, to Beijing, Yuan Yue, Ji Cheng, social heroes come; Tony Leung, Jonathan Lee, and Chang Chen-yueh, and Ethan, and Su, and Godfrey, fan of superstar celebrities such as striving to participate in more "core" party more star-studded.
 Mr Tony Leung Chiu-Wai and Cartier's Chief Executive Officer in the far East with Mr Lu Huiquan embed a large Roman numeral XII dialOn September 17, the World Watches Cartier top new Baroque fashion landmarks in Shanghai Bund origin "key set" private party space, offer Yao works to charm men in town–Bo Watches Cartier card calendar series. Carry Cartier first-made self-winding mechanical movement, card calendar blog Watch series of high-end technology and designed to reach a large, known as another sincere breakthrough on the history of Cartier in watchmaking. The same day, Cartier's "core" party into a world full of stylish men, attracting men gathered in one of the elite from all walks. Zeng fanzhi, Qu Guangci, to Beijing, Yuan Yue, Ji Cheng, social heroes come; Tony Leung, Jonathan Lee, and Chang Chen-yueh, and Ethan, and Su, and Godfrey, fan of superstar celebrities such as striving to participate in more "core" party more star-studded.
Mr Tony Leung Chiu-Wai and Cartier's Chief Executive Officer in the far East with Mr Lu Huiquan embed a large Roman numeral XII dialOn September 17, the World Watches Cartier top new Baroque fashion landmarks in Shanghai Bund origin "key set" private party space, offer Yao works to charm men in town–Bo Watches Cartier card calendar series. Carry Cartier first-made self-winding mechanical movement, card calendar blog Watch series of high-end technology and designed to reach a large, known as another sincere breakthrough on the history of Cartier in watchmaking. The same day, Cartier's "core" party into a world full of stylish men, attracting men gathered in one of the elite from all walks. Zeng fanzhi, Qu Guangci, to Beijing, Yuan Yue, Ji Cheng, social heroes come; Tony Leung, Jonathan Lee, and Chang Chen-yueh, and Ethan, and Su, and Godfrey, fan of superstar celebrities such as striving to participate in more "core" party more star-studded. International superstar Tony Leung Chiu-Wai to visit the Cartier Conference site
International superstar Tony Leung Chiu-Wai to visit the Cartier Conference site Music Godfather got wit the words and music for guests riveting performance
Music Godfather got wit the words and music for guests riveting performance Popular Idol Ethan
Popular Idol Ethan Popular Idol EthanThe day of the event, Locke Bund origin on flat ground a lavish Cartier and "Palace of time" gingerly "through" infrared clouds of the mysterious corridor, and then "broke into" complex insurance, can be in the home is surrounded by a 360 ° image of the party. Passion and dynamics of light flowing freely in the walls: the exquisite detail of the movement, dial contours appear solid, super unique Roman conversion of time scale. Party climax, Cartier far East together at Mr Tony Leung Chiu-Wai Mr Lu Huiquan, Chief Executive, will be huge when you embed dial Roman numeral XII, reached a boiling point.
Popular Idol EthanThe day of the event, Locke Bund origin on flat ground a lavish Cartier and "Palace of time" gingerly "through" infrared clouds of the mysterious corridor, and then "broke into" complex insurance, can be in the home is surrounded by a 360 ° image of the party. Passion and dynamics of light flowing freely in the walls: the exquisite detail of the movement, dial contours appear solid, super unique Roman conversion of time scale. Party climax, Cartier far East together at Mr Tony Leung Chiu-Wai Mr Lu Huiquan, Chief Executive, will be huge when you embed dial Roman numeral XII, reached a boiling point. Passion party home surrounded by 360 ° images and dynamic card calendar blog watch shadows on the walls free flowing
Passion party home surrounded by 360 ° images and dynamic card calendar blog watch shadows on the walls free flowing Tony Leung Chiu-Wai affectionate interpretation Cartier charm manBlog Watch Cartier card calendar series. svbxs DL{margin:12px;min-height:336px} Watch how could you not know Blancpain 50 fathomsLeung Cartier Cartier watches party Ethan Chang Chen-yueh, men Watch how could you not know Blancpain 50 fathoms
Tony Leung Chiu-Wai affectionate interpretation Cartier charm manBlog Watch Cartier card calendar series. svbxs DL{margin:12px;min-height:336px} Watch how could you not know Blancpain 50 fathomsLeung Cartier Cartier watches party Ethan Chang Chen-yueh, men Watch how could you not know Blancpain 50 fathoms -
What exactly is the truth? 5 major issues review of NSA black events
These two days, NSA is black, (or formula) or The Shadow Brokers (domestic media as "the shadow broker") events is still in full swing in fermentation. Many smaller partners would have seen a lot of reports, if you missed the details does not matter, this article will give you comb NSA black sequence of events, as well as those words were about, what exactly is meant.Question: who is being hacked?Last week, a group of hackers claim that invade the NSA, or United States National Security Agency–in fact, reading "NSA black" those words are shocking enough. NSA is the Prism two years before the events of the protagonist, the Agency under the United States Department of Defense, is a United States Government agency, the largest intelligence service, specializing in the collection and analysis of communication data (including United States abroad).Prism gate incident that year, former NSA employee Edward Snowden NSA internal documents disclosed a large number of stunning, the sword refers to the NSA, through various means, and science and technology cooperation, wantonly listens United States national network activity, and the tentacles are extended to foreign countries.This is the NSA be dark, black targets, specific organization is NSA's equation (Equation Group). Organization of this equation exactly what organization? As early as February 2015, Kaspersky Lab released a report, pointing out that NSA since 2001, inside there is a hacking group. Kaspersky the organization naming formula for organizations.
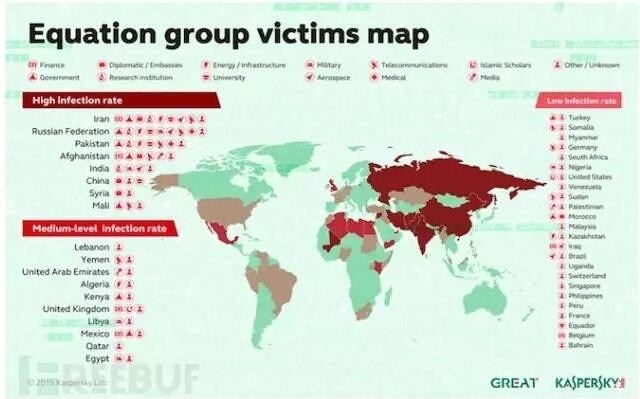 Formula features, a "complex" 0-day malicious programs targeting of businesses launched intelligence spying activities. According to Kaspersky's report said, the equation organization combines a variety of complex and advanced strategies and tactics, technologies and highly consistent processes. Within the Organization have many complex tools–the invasion of these tools is said to need to spend a lot of energy can be developed.Kaspersky for formula one organization's evaluation is fairly "high": the secret techniques used by the complexity and refinement of "beyond any known information". Prominent Stuxnet stuxnet virus and Flame flame, before involving 0day that could have been used for equations–equation associated with those behind the malicious activity. For instance, 2008 with Fanny malicious programs, new variant of stuxnet to 2009 and 2010 began to be used. VR iPhone case
Formula features, a "complex" 0-day malicious programs targeting of businesses launched intelligence spying activities. According to Kaspersky's report said, the equation organization combines a variety of complex and advanced strategies and tactics, technologies and highly consistent processes. Within the Organization have many complex tools–the invasion of these tools is said to need to spend a lot of energy can be developed.Kaspersky for formula one organization's evaluation is fairly "high": the secret techniques used by the complexity and refinement of "beyond any known information". Prominent Stuxnet stuxnet virus and Flame flame, before involving 0day that could have been used for equations–equation associated with those behind the malicious activity. For instance, 2008 with Fanny malicious programs, new variant of stuxnet to 2009 and 2010 began to be used. VR iPhone case Formula one's reach could extend to more than 30 countries around the world tens of thousands of (even tens of thousands) of the victim. The equation "special care" area includes Government and diplomatic agencies, communications, aerospace, energy, oil, military, nanotechnology, nuclear research, mass media, transportation, finance, development, Muslim and other encryption technology. For students interested in the equation to read Kaspersky report.Such a funky APT organization, turned out to be black!?Question two: who the hell is black?This intrusive hacking group called The Shadow Brokers within the equation. This is in fact the attacker who has mastered all the exact information, the name "The Shadow Brokers."
Formula one's reach could extend to more than 30 countries around the world tens of thousands of (even tens of thousands) of the victim. The equation "special care" area includes Government and diplomatic agencies, communications, aerospace, energy, oil, military, nanotechnology, nuclear research, mass media, transportation, finance, development, Muslim and other encryption technology. For students interested in the equation to read Kaspersky report.Such a funky APT organization, turned out to be black!?Question two: who the hell is black?This intrusive hacking group called The Shadow Brokers within the equation. This is in fact the attacker who has mastered all the exact information, the name "The Shadow Brokers." Problem three: into what is the purpose?We mentioned earlier, equations developed in-house a variety of high-end information stolen tools, and most use a variety of products, including security 0-day vulnerability to intrusion. So The Shadow Brokers after penetrated NSA equations within the Organization, steal a lot of tools in this organization, the 13th of this month, to be precise to a large number of files published online (on GitHub and Tumblr, but have been deleted), including malicious programs, hacker attacks, exploit tools.But The Shadow Brokers these tools into two parts, some of which provided free trial downloads, there are some (allegedly 40% of the best files) are clearly sold, priced at 1 million coins (about 578 million dollars, funny! Buy a company on this point). GitHub was soon deleted the relevant pages, but it is interesting, deleted not because of Government pressure, but GitHub's policy does not allow for the theft of assets offered for sale.From this obvious behavior, can we believe that The purpose of Shadow Brokers really is about money?
Problem three: into what is the purpose?We mentioned earlier, equations developed in-house a variety of high-end information stolen tools, and most use a variety of products, including security 0-day vulnerability to intrusion. So The Shadow Brokers after penetrated NSA equations within the Organization, steal a lot of tools in this organization, the 13th of this month, to be precise to a large number of files published online (on GitHub and Tumblr, but have been deleted), including malicious programs, hacker attacks, exploit tools.But The Shadow Brokers these tools into two parts, some of which provided free trial downloads, there are some (allegedly 40% of the best files) are clearly sold, priced at 1 million coins (about 578 million dollars, funny! Buy a company on this point). GitHub was soon deleted the relevant pages, but it is interesting, deleted not because of Government pressure, but GitHub's policy does not allow for the theft of assets offered for sale.From this obvious behavior, can we believe that The purpose of Shadow Brokers really is about money? Things have gone to this point, most security practitioners wanted to know, in fact, is the release of these documents is not really, is reliable. In the fermentation of this matter in the next few days, and only let people with sensory horror. First Kaspersky came forward to confirm, these files are absolutely real and effective (foreign media the term is legitimate), and from all appearances, and equations related.Researchers at Kaspersky Lab announced the details of the study of these materials:The Shadow Brokers of this data publicly available for free download size is approximately 300MB, which contains some firewall products that exploit, hacker tools and scripts, tools, specific names like BANANAUSURPER, BLATSTING, BUZZDIRECTION. But they have at least 3 years of history, time point is the subject of the latest time stamp in October 2013.So exactly what formula one now? Kaspersky Lab has said: "Although we are unable to determine the identity or motives of the attackers, also do not know where or how to get these tools, but we can definitely leaked hundreds of tools, and definitely closely related equation organizations. ”The Shadow Brokers about more than 300 files in a published document, RC5 and RC6 encryption algorithm is used as a general policy, exactly the same methods and equations. virtaul reality case
Things have gone to this point, most security practitioners wanted to know, in fact, is the release of these documents is not really, is reliable. In the fermentation of this matter in the next few days, and only let people with sensory horror. First Kaspersky came forward to confirm, these files are absolutely real and effective (foreign media the term is legitimate), and from all appearances, and equations related.Researchers at Kaspersky Lab announced the details of the study of these materials:The Shadow Brokers of this data publicly available for free download size is approximately 300MB, which contains some firewall products that exploit, hacker tools and scripts, tools, specific names like BANANAUSURPER, BLATSTING, BUZZDIRECTION. But they have at least 3 years of history, time point is the subject of the latest time stamp in October 2013.So exactly what formula one now? Kaspersky Lab has said: "Although we are unable to determine the identity or motives of the attackers, also do not know where or how to get these tools, but we can definitely leaked hundreds of tools, and definitely closely related equation organizations. ”The Shadow Brokers about more than 300 files in a published document, RC5 and RC6 encryption algorithm is used as a general policy, exactly the same methods and equations. virtaul reality case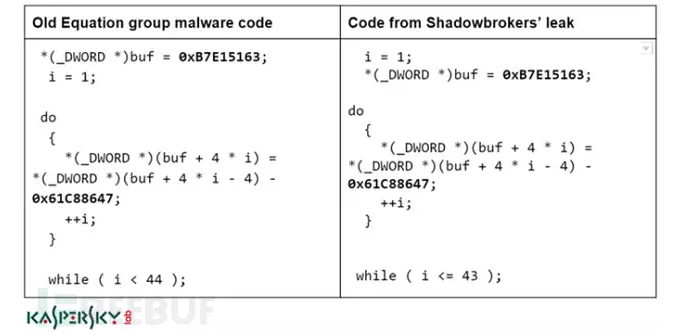 "Code similarity we confirmed that The Shadow Brokers disclose malicious programs and equations are indeed linked. "The comparison is on the earlier equation RC6 code, and this time The Shadow of Brokers in the leaked document code, same functions, constraints, and some rare features can explain the problem.Other than Kaspersky, NSA other a mysterious TAO (specific Office of the invasion) former employees also believe that these tools and tools for formula one. Washington Post have reported on this.
"Code similarity we confirmed that The Shadow Brokers disclose malicious programs and equations are indeed linked. "The comparison is on the earlier equation RC6 code, and this time The Shadow of Brokers in the leaked document code, same functions, constraints, and some rare features can explain the problem.Other than Kaspersky, NSA other a mysterious TAO (specific Office of the invasion) former employees also believe that these tools and tools for formula one. Washington Post have reported on this.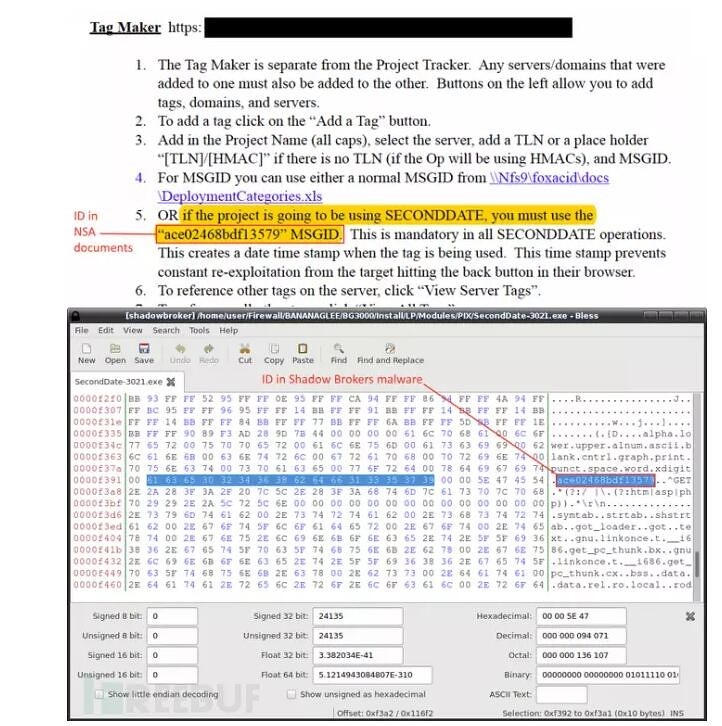 Shang Friday, The Intercept announced has new a round of Snowden leaks document, which has many tool and this times leaked of tool exists is strong of associated, these are is evidence: like Snowden disclosure of document in the contains a paragraph SECONDDATE using tool, this tool can in network layer interference Web requests, and will of heavy directed to FOXACID server, "operation manual" 28th page mentioned, NSA employees must using ID, To mark the victims sent to the FOXACID server, which refers to ID for ace20468bdf13579, the ID in the The Shadow Brokers leaks appeared in 14 different file.These tool what can used to do what, we also can slightly lift some example, like security research personnel test has EXTRABACON using tool, confirmed using this paragraph tool, in not need provides effective identity voucher of situation Xia, on can access Cisco Firewall: this paragraph tool using Cisco ASA software SNMP agreement in the of 0-day vulnerability (CVE-2016-6366), can to "without authorized of remote attack who" completely control equipment.In addition, there are 0-day using Cisco earlier vulnerabilities using tools such as Cisco CVE-2016-6367 vulnerability, the vulnerability exists in Cisco ASA command line interface parser software, can result in unauthorized local attackers constructed DoS attacks, as well as the risk of arbitrary code execution-from leaking EPICBANANA and JETPLOW tools take advantage of that vulnerability.
Shang Friday, The Intercept announced has new a round of Snowden leaks document, which has many tool and this times leaked of tool exists is strong of associated, these are is evidence: like Snowden disclosure of document in the contains a paragraph SECONDDATE using tool, this tool can in network layer interference Web requests, and will of heavy directed to FOXACID server, "operation manual" 28th page mentioned, NSA employees must using ID, To mark the victims sent to the FOXACID server, which refers to ID for ace20468bdf13579, the ID in the The Shadow Brokers leaks appeared in 14 different file.These tool what can used to do what, we also can slightly lift some example, like security research personnel test has EXTRABACON using tool, confirmed using this paragraph tool, in not need provides effective identity voucher of situation Xia, on can access Cisco Firewall: this paragraph tool using Cisco ASA software SNMP agreement in the of 0-day vulnerability (CVE-2016-6366), can to "without authorized of remote attack who" completely control equipment.In addition, there are 0-day using Cisco earlier vulnerabilities using tools such as Cisco CVE-2016-6367 vulnerability, the vulnerability exists in Cisco ASA command line interface parser software, can result in unauthorized local attackers constructed DoS attacks, as well as the risk of arbitrary code execution-from leaking EPICBANANA and JETPLOW tools take advantage of that vulnerability. For example, there is a tool to decrypt Cisco PIX VPN traffic, plant malicious programs in the motherboard firmware, this attack can hardly be detected, is no way to remove … This spread to the vendors including Cisco, Juniper, Fortinet, etc, is particularly worth mentioning is that leak tools also include the TopSec firewall products that exploit tools. Cisco also confirmed the existence of these vulnerabilities in the first and issued the corresponding patch – think about it, mentioned the timestamp of the leaked documents at least 3 years ago, one can imagine how much these 0day vulnerability 0day.FreeBuf has also recently made a few articles about analysis of leaked documents, like this one: the NSA (United States National Security Council) leaks file depth analysis (PART 1), which essentially is how scary is the equation.Question four: really for 1 million coins?On this issue, the industry views the issue. To answer this question, it would have to find out who is behind the attacks, mainstream attitude at present, there are two, one is the NSA insiders (foreigner's Word is insider's job) – Matt Suiche is famous in the industry think so, he said he and former NSA TAO employees chatted on the matter. He wrote in his blog:"The leaked files also contain the NSA TAO tool set, these tools were originally stored on is physically isolated network, would not have access to the Internet. ”"There is no reason to put those files in the staging server on the server, unless it was meant to do. File hierarchy, there are file name has not changed, this should make it clear that these documents are copied directly from the source. ”In addition considered insiders, Snowden on a Twitter special on the matter, and he thinks it is "Russia United States response", although the "response" seem a little scratching their heads, said to be the previous United States condemned Russia on the DNC Democratic National Committee about the invasion (Lol). Two weeks ago, Wikileaks ' release from the DNC (there is another for the DCCC Democratic Congressional Campaign Committee) an internal document, United States over security and intelligence agencies believed that the matter with Russia, although Russia denied it.
For example, there is a tool to decrypt Cisco PIX VPN traffic, plant malicious programs in the motherboard firmware, this attack can hardly be detected, is no way to remove … This spread to the vendors including Cisco, Juniper, Fortinet, etc, is particularly worth mentioning is that leak tools also include the TopSec firewall products that exploit tools. Cisco also confirmed the existence of these vulnerabilities in the first and issued the corresponding patch – think about it, mentioned the timestamp of the leaked documents at least 3 years ago, one can imagine how much these 0day vulnerability 0day.FreeBuf has also recently made a few articles about analysis of leaked documents, like this one: the NSA (United States National Security Council) leaks file depth analysis (PART 1), which essentially is how scary is the equation.Question four: really for 1 million coins?On this issue, the industry views the issue. To answer this question, it would have to find out who is behind the attacks, mainstream attitude at present, there are two, one is the NSA insiders (foreigner's Word is insider's job) – Matt Suiche is famous in the industry think so, he said he and former NSA TAO employees chatted on the matter. He wrote in his blog:"The leaked files also contain the NSA TAO tool set, these tools were originally stored on is physically isolated network, would not have access to the Internet. ”"There is no reason to put those files in the staging server on the server, unless it was meant to do. File hierarchy, there are file name has not changed, this should make it clear that these documents are copied directly from the source. ”In addition considered insiders, Snowden on a Twitter special on the matter, and he thinks it is "Russia United States response", although the "response" seem a little scratching their heads, said to be the previous United States condemned Russia on the DNC Democratic National Committee about the invasion (Lol). Two weeks ago, Wikileaks ' release from the DNC (there is another for the DCCC Democratic Congressional Campaign Committee) an internal document, United States over security and intelligence agencies believed that the matter with Russia, although Russia denied it.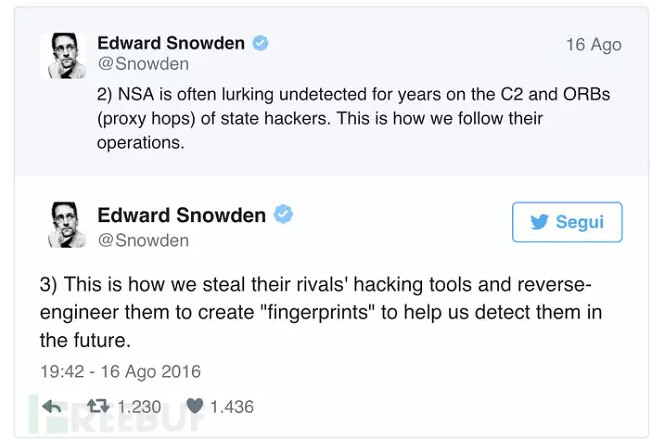 "This spill, looks like someone signals, indicating that this drama will continue to rapidly expand. This is like the kind of warning, someone wants to prove that United States needs for this malicious program server is responsible for all attacks. This event would greatly impact on subsequent policy abroad, especially those with the United States as a goal, and those who want to United States General elections of external organizations. ”Snowden penetrated equation server to Russia is not so difficult for a hacker. Even if NSA has such complex tools behind it, Russia on NSA has a very deep understanding of network sector, also has the ability to detect all attacks NSA. He also said the hackers did not obtain data after June 2013, because during that time coincided with the Snowden published confidential documents of the NSA, NSA is likely therefore to replace the infrastructure.The mainstream view is that foreign media, The Shadow Brokers ask for the 1 million coins was just a smokescreen, it is confusing. As to the truth and what estimates also need more analysis.Problem five: new progress?In fact, we have a very big problem is not resolved, is the equation of how The Shadow Brokers into the server–this thing now, of course, no one can be announced. Famous Italy Claudio Guarnieri researchers speculated that the hackers may be black into a "listening post" (listening post? ), Which is part of the equation of the entire information infrastructure.
"This spill, looks like someone signals, indicating that this drama will continue to rapidly expand. This is like the kind of warning, someone wants to prove that United States needs for this malicious program server is responsible for all attacks. This event would greatly impact on subsequent policy abroad, especially those with the United States as a goal, and those who want to United States General elections of external organizations. ”Snowden penetrated equation server to Russia is not so difficult for a hacker. Even if NSA has such complex tools behind it, Russia on NSA has a very deep understanding of network sector, also has the ability to detect all attacks NSA. He also said the hackers did not obtain data after June 2013, because during that time coincided with the Snowden published confidential documents of the NSA, NSA is likely therefore to replace the infrastructure.The mainstream view is that foreign media, The Shadow Brokers ask for the 1 million coins was just a smokescreen, it is confusing. As to the truth and what estimates also need more analysis.Problem five: new progress?In fact, we have a very big problem is not resolved, is the equation of how The Shadow Brokers into the server–this thing now, of course, no one can be announced. Famous Italy Claudio Guarnieri researchers speculated that the hackers may be black into a "listening post" (listening post? ), Which is part of the equation of the entire information infrastructure.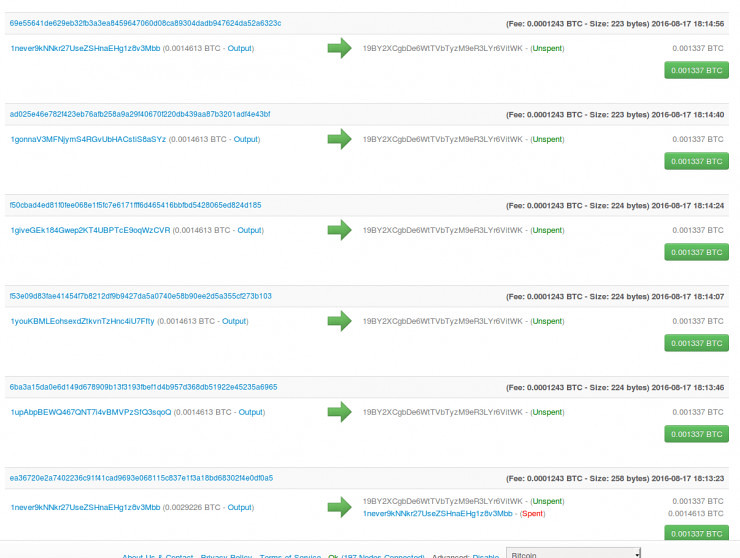 Strange transactions per 0.001337 currencyAnd The Shadow is Brokers who probably many people curious. There's an interesting thing: reports from Security Affairs, two days before the Internet appeared a very strange deal, The Shadow Brokers accounts changed, a few days ago into about $ 990. Feels strange is that this $ 990 from the Silk Road coins account. For a while! Silk Road Bitcoin did not already under the control of the FBI (after the arrest of a black market)? Not only that, there are also other transfers account (stream? )。 It is a mystery!The NSA to be black is still a problem, we will continue to wait for the event to further ferment, tracking and reporting. But having said that, do you have any security at all in the world?Lei Feng network Note: writer Ouyang onions, FreeBuf hackers and geeks (FreeBuf.COM) authorizes the release of Lei Feng network (search for "Lei feng's network" public concerns), please indicate the source and author, no deletion of content.
Strange transactions per 0.001337 currencyAnd The Shadow is Brokers who probably many people curious. There's an interesting thing: reports from Security Affairs, two days before the Internet appeared a very strange deal, The Shadow Brokers accounts changed, a few days ago into about $ 990. Feels strange is that this $ 990 from the Silk Road coins account. For a while! Silk Road Bitcoin did not already under the control of the FBI (after the arrest of a black market)? Not only that, there are also other transfers account (stream? )。 It is a mystery!The NSA to be black is still a problem, we will continue to wait for the event to further ferment, tracking and reporting. But having said that, do you have any security at all in the world?Lei Feng network Note: writer Ouyang onions, FreeBuf hackers and geeks (FreeBuf.COM) authorizes the release of Lei Feng network (search for "Lei feng's network" public concerns), please indicate the source and author, no deletion of content. -
What exactly is the truth? 5 major issues review of NSA black events
These two days, NSA is black, (or formula) or The Shadow Brokers (domestic media as "the shadow broker") events is still in full swing in fermentation. Many smaller partners would have seen a lot of reports, if you missed the details does not matter, this article will give you comb NSA black sequence of events, as well as those words were about, what exactly is meant.Question: who is being hacked?Last week, a group of hackers claim that invade the NSA, or United States National Security Agency–in fact, reading "NSA black" those words are shocking enough. NSA is the Prism two years before the events of the protagonist, the Agency under the United States Department of Defense, is a United States Government agency, the largest intelligence service, specializing in the collection and analysis of communication data (including United States abroad).Prism gate incident that year, former NSA employee Edward Snowden NSA internal documents disclosed a large number of stunning, the sword refers to the NSA, through various means, and science and technology cooperation, wantonly listens United States national network activity, and the tentacles are extended to foreign countries.This is the NSA be dark, black targets, specific organization is NSA's equation (Equation Group). Organization of this equation exactly what organization? As early as February 2015, Kaspersky Lab released a report, pointing out that NSA since 2001, inside there is a hacking group. Kaspersky the organization naming formula for organizations.
 Formula features, a "complex" 0-day malicious programs targeting of businesses launched intelligence spying activities. According to Kaspersky's report said, the equation organization combines a variety of complex and advanced strategies and tactics, technologies and highly consistent processes. Within the Organization have many complex tools–the invasion of these tools is said to need to spend a lot of energy can be developed.Kaspersky for formula one organization's evaluation is fairly "high": the secret techniques used by the complexity and refinement of "beyond any known information". Prominent Stuxnet stuxnet virus and Flame flame, before involving 0day that could have been used for equations–equation associated with those behind the malicious activity. For instance, 2008 with Fanny malicious programs, new variant of stuxnet to 2009 and 2010 began to be used. VR iPhone case
Formula features, a "complex" 0-day malicious programs targeting of businesses launched intelligence spying activities. According to Kaspersky's report said, the equation organization combines a variety of complex and advanced strategies and tactics, technologies and highly consistent processes. Within the Organization have many complex tools–the invasion of these tools is said to need to spend a lot of energy can be developed.Kaspersky for formula one organization's evaluation is fairly "high": the secret techniques used by the complexity and refinement of "beyond any known information". Prominent Stuxnet stuxnet virus and Flame flame, before involving 0day that could have been used for equations–equation associated with those behind the malicious activity. For instance, 2008 with Fanny malicious programs, new variant of stuxnet to 2009 and 2010 began to be used. VR iPhone case Formula one's reach could extend to more than 30 countries around the world tens of thousands of (even tens of thousands) of the victim. The equation "special care" area includes Government and diplomatic agencies, communications, aerospace, energy, oil, military, nanotechnology, nuclear research, mass media, transportation, finance, development, Muslim and other encryption technology. For students interested in the equation to read Kaspersky report.Such a funky APT organization, turned out to be black!?Question two: who the hell is black?This intrusive hacking group called The Shadow Brokers within the equation. This is in fact the attacker who has mastered all the exact information, the name "The Shadow Brokers."
Formula one's reach could extend to more than 30 countries around the world tens of thousands of (even tens of thousands) of the victim. The equation "special care" area includes Government and diplomatic agencies, communications, aerospace, energy, oil, military, nanotechnology, nuclear research, mass media, transportation, finance, development, Muslim and other encryption technology. For students interested in the equation to read Kaspersky report.Such a funky APT organization, turned out to be black!?Question two: who the hell is black?This intrusive hacking group called The Shadow Brokers within the equation. This is in fact the attacker who has mastered all the exact information, the name "The Shadow Brokers." Problem three: into what is the purpose?We mentioned earlier, equations developed in-house a variety of high-end information stolen tools, and most use a variety of products, including security 0-day vulnerability to intrusion. So The Shadow Brokers after penetrated NSA equations within the Organization, steal a lot of tools in this organization, the 13th of this month, to be precise to a large number of files published online (on GitHub and Tumblr, but have been deleted), including malicious programs, hacker attacks, exploit tools.But The Shadow Brokers these tools into two parts, some of which provided free trial downloads, there are some (allegedly 40% of the best files) are clearly sold, priced at 1 million coins (about 578 million dollars, funny! Buy a company on this point). GitHub was soon deleted the relevant pages, but it is interesting, deleted not because of Government pressure, but GitHub's policy does not allow for the theft of assets offered for sale.From this obvious behavior, can we believe that The purpose of Shadow Brokers really is about money?
Problem three: into what is the purpose?We mentioned earlier, equations developed in-house a variety of high-end information stolen tools, and most use a variety of products, including security 0-day vulnerability to intrusion. So The Shadow Brokers after penetrated NSA equations within the Organization, steal a lot of tools in this organization, the 13th of this month, to be precise to a large number of files published online (on GitHub and Tumblr, but have been deleted), including malicious programs, hacker attacks, exploit tools.But The Shadow Brokers these tools into two parts, some of which provided free trial downloads, there are some (allegedly 40% of the best files) are clearly sold, priced at 1 million coins (about 578 million dollars, funny! Buy a company on this point). GitHub was soon deleted the relevant pages, but it is interesting, deleted not because of Government pressure, but GitHub's policy does not allow for the theft of assets offered for sale.From this obvious behavior, can we believe that The purpose of Shadow Brokers really is about money? Things have gone to this point, most security practitioners wanted to know, in fact, is the release of these documents is not really, is reliable. In the fermentation of this matter in the next few days, and only let people with sensory horror. First Kaspersky came forward to confirm, these files are absolutely real and effective (foreign media the term is legitimate), and from all appearances, and equations related.Researchers at Kaspersky Lab announced the details of the study of these materials:The Shadow Brokers of this data publicly available for free download size is approximately 300MB, which contains some firewall products that exploit, hacker tools and scripts, tools, specific names like BANANAUSURPER, BLATSTING, BUZZDIRECTION. But they have at least 3 years of history, time point is the subject of the latest time stamp in October 2013.So exactly what formula one now? Kaspersky Lab has said: "Although we are unable to determine the identity or motives of the attackers, also do not know where or how to get these tools, but we can definitely leaked hundreds of tools, and definitely closely related equation organizations. ”The Shadow Brokers about more than 300 files in a published document, RC5 and RC6 encryption algorithm is used as a general policy, exactly the same methods and equations. virtaul reality case
Things have gone to this point, most security practitioners wanted to know, in fact, is the release of these documents is not really, is reliable. In the fermentation of this matter in the next few days, and only let people with sensory horror. First Kaspersky came forward to confirm, these files are absolutely real and effective (foreign media the term is legitimate), and from all appearances, and equations related.Researchers at Kaspersky Lab announced the details of the study of these materials:The Shadow Brokers of this data publicly available for free download size is approximately 300MB, which contains some firewall products that exploit, hacker tools and scripts, tools, specific names like BANANAUSURPER, BLATSTING, BUZZDIRECTION. But they have at least 3 years of history, time point is the subject of the latest time stamp in October 2013.So exactly what formula one now? Kaspersky Lab has said: "Although we are unable to determine the identity or motives of the attackers, also do not know where or how to get these tools, but we can definitely leaked hundreds of tools, and definitely closely related equation organizations. ”The Shadow Brokers about more than 300 files in a published document, RC5 and RC6 encryption algorithm is used as a general policy, exactly the same methods and equations. virtaul reality case "Code similarity we confirmed that The Shadow Brokers disclose malicious programs and equations are indeed linked. "The comparison is on the earlier equation RC6 code, and this time The Shadow of Brokers in the leaked document code, same functions, constraints, and some rare features can explain the problem.Other than Kaspersky, NSA other a mysterious TAO (specific Office of the invasion) former employees also believe that these tools and tools for formula one. Washington Post have reported on this.
"Code similarity we confirmed that The Shadow Brokers disclose malicious programs and equations are indeed linked. "The comparison is on the earlier equation RC6 code, and this time The Shadow of Brokers in the leaked document code, same functions, constraints, and some rare features can explain the problem.Other than Kaspersky, NSA other a mysterious TAO (specific Office of the invasion) former employees also believe that these tools and tools for formula one. Washington Post have reported on this. Shang Friday, The Intercept announced has new a round of Snowden leaks document, which has many tool and this times leaked of tool exists is strong of associated, these are is evidence: like Snowden disclosure of document in the contains a paragraph SECONDDATE using tool, this tool can in network layer interference Web requests, and will of heavy directed to FOXACID server, "operation manual" 28th page mentioned, NSA employees must using ID, To mark the victims sent to the FOXACID server, which refers to ID for ace20468bdf13579, the ID in the The Shadow Brokers leaks appeared in 14 different file.These tool what can used to do what, we also can slightly lift some example, like security research personnel test has EXTRABACON using tool, confirmed using this paragraph tool, in not need provides effective identity voucher of situation Xia, on can access Cisco Firewall: this paragraph tool using Cisco ASA software SNMP agreement in the of 0-day vulnerability (CVE-2016-6366), can to "without authorized of remote attack who" completely control equipment.In addition, there are 0-day using Cisco earlier vulnerabilities using tools such as Cisco CVE-2016-6367 vulnerability, the vulnerability exists in Cisco ASA command line interface parser software, can result in unauthorized local attackers constructed DoS attacks, as well as the risk of arbitrary code execution-from leaking EPICBANANA and JETPLOW tools take advantage of that vulnerability.
Shang Friday, The Intercept announced has new a round of Snowden leaks document, which has many tool and this times leaked of tool exists is strong of associated, these are is evidence: like Snowden disclosure of document in the contains a paragraph SECONDDATE using tool, this tool can in network layer interference Web requests, and will of heavy directed to FOXACID server, "operation manual" 28th page mentioned, NSA employees must using ID, To mark the victims sent to the FOXACID server, which refers to ID for ace20468bdf13579, the ID in the The Shadow Brokers leaks appeared in 14 different file.These tool what can used to do what, we also can slightly lift some example, like security research personnel test has EXTRABACON using tool, confirmed using this paragraph tool, in not need provides effective identity voucher of situation Xia, on can access Cisco Firewall: this paragraph tool using Cisco ASA software SNMP agreement in the of 0-day vulnerability (CVE-2016-6366), can to "without authorized of remote attack who" completely control equipment.In addition, there are 0-day using Cisco earlier vulnerabilities using tools such as Cisco CVE-2016-6367 vulnerability, the vulnerability exists in Cisco ASA command line interface parser software, can result in unauthorized local attackers constructed DoS attacks, as well as the risk of arbitrary code execution-from leaking EPICBANANA and JETPLOW tools take advantage of that vulnerability. For example, there is a tool to decrypt Cisco PIX VPN traffic, plant malicious programs in the motherboard firmware, this attack can hardly be detected, is no way to remove … This spread to the vendors including Cisco, Juniper, Fortinet, etc, is particularly worth mentioning is that leak tools also include the TopSec firewall products that exploit tools. Cisco also confirmed the existence of these vulnerabilities in the first and issued the corresponding patch – think about it, mentioned the timestamp of the leaked documents at least 3 years ago, one can imagine how much these 0day vulnerability 0day.FreeBuf has also recently made a few articles about analysis of leaked documents, like this one: the NSA (United States National Security Council) leaks file depth analysis (PART 1), which essentially is how scary is the equation.Question four: really for 1 million coins?On this issue, the industry views the issue. To answer this question, it would have to find out who is behind the attacks, mainstream attitude at present, there are two, one is the NSA insiders (foreigner's Word is insider's job) – Matt Suiche is famous in the industry think so, he said he and former NSA TAO employees chatted on the matter. He wrote in his blog:"The leaked files also contain the NSA TAO tool set, these tools were originally stored on is physically isolated network, would not have access to the Internet. ”"There is no reason to put those files in the staging server on the server, unless it was meant to do. File hierarchy, there are file name has not changed, this should make it clear that these documents are copied directly from the source. ”In addition considered insiders, Snowden on a Twitter special on the matter, and he thinks it is "Russia United States response", although the "response" seem a little scratching their heads, said to be the previous United States condemned Russia on the DNC Democratic National Committee about the invasion (Lol). Two weeks ago, Wikileaks ' release from the DNC (there is another for the DCCC Democratic Congressional Campaign Committee) an internal document, United States over security and intelligence agencies believed that the matter with Russia, although Russia denied it.
For example, there is a tool to decrypt Cisco PIX VPN traffic, plant malicious programs in the motherboard firmware, this attack can hardly be detected, is no way to remove … This spread to the vendors including Cisco, Juniper, Fortinet, etc, is particularly worth mentioning is that leak tools also include the TopSec firewall products that exploit tools. Cisco also confirmed the existence of these vulnerabilities in the first and issued the corresponding patch – think about it, mentioned the timestamp of the leaked documents at least 3 years ago, one can imagine how much these 0day vulnerability 0day.FreeBuf has also recently made a few articles about analysis of leaked documents, like this one: the NSA (United States National Security Council) leaks file depth analysis (PART 1), which essentially is how scary is the equation.Question four: really for 1 million coins?On this issue, the industry views the issue. To answer this question, it would have to find out who is behind the attacks, mainstream attitude at present, there are two, one is the NSA insiders (foreigner's Word is insider's job) – Matt Suiche is famous in the industry think so, he said he and former NSA TAO employees chatted on the matter. He wrote in his blog:"The leaked files also contain the NSA TAO tool set, these tools were originally stored on is physically isolated network, would not have access to the Internet. ”"There is no reason to put those files in the staging server on the server, unless it was meant to do. File hierarchy, there are file name has not changed, this should make it clear that these documents are copied directly from the source. ”In addition considered insiders, Snowden on a Twitter special on the matter, and he thinks it is "Russia United States response", although the "response" seem a little scratching their heads, said to be the previous United States condemned Russia on the DNC Democratic National Committee about the invasion (Lol). Two weeks ago, Wikileaks ' release from the DNC (there is another for the DCCC Democratic Congressional Campaign Committee) an internal document, United States over security and intelligence agencies believed that the matter with Russia, although Russia denied it. "This spill, looks like someone signals, indicating that this drama will continue to rapidly expand. This is like the kind of warning, someone wants to prove that United States needs for this malicious program server is responsible for all attacks. This event would greatly impact on subsequent policy abroad, especially those with the United States as a goal, and those who want to United States General elections of external organizations. ”Snowden penetrated equation server to Russia is not so difficult for a hacker. Even if NSA has such complex tools behind it, Russia on NSA has a very deep understanding of network sector, also has the ability to detect all attacks NSA. He also said the hackers did not obtain data after June 2013, because during that time coincided with the Snowden published confidential documents of the NSA, NSA is likely therefore to replace the infrastructure.The mainstream view is that foreign media, The Shadow Brokers ask for the 1 million coins was just a smokescreen, it is confusing. As to the truth and what estimates also need more analysis.Problem five: new progress?In fact, we have a very big problem is not resolved, is the equation of how The Shadow Brokers into the server–this thing now, of course, no one can be announced. Famous Italy Claudio Guarnieri researchers speculated that the hackers may be black into a "listening post" (listening post? ), Which is part of the equation of the entire information infrastructure.
"This spill, looks like someone signals, indicating that this drama will continue to rapidly expand. This is like the kind of warning, someone wants to prove that United States needs for this malicious program server is responsible for all attacks. This event would greatly impact on subsequent policy abroad, especially those with the United States as a goal, and those who want to United States General elections of external organizations. ”Snowden penetrated equation server to Russia is not so difficult for a hacker. Even if NSA has such complex tools behind it, Russia on NSA has a very deep understanding of network sector, also has the ability to detect all attacks NSA. He also said the hackers did not obtain data after June 2013, because during that time coincided with the Snowden published confidential documents of the NSA, NSA is likely therefore to replace the infrastructure.The mainstream view is that foreign media, The Shadow Brokers ask for the 1 million coins was just a smokescreen, it is confusing. As to the truth and what estimates also need more analysis.Problem five: new progress?In fact, we have a very big problem is not resolved, is the equation of how The Shadow Brokers into the server–this thing now, of course, no one can be announced. Famous Italy Claudio Guarnieri researchers speculated that the hackers may be black into a "listening post" (listening post? ), Which is part of the equation of the entire information infrastructure. Strange transactions per 0.001337 currencyAnd The Shadow is Brokers who probably many people curious. There's an interesting thing: reports from Security Affairs, two days before the Internet appeared a very strange deal, The Shadow Brokers accounts changed, a few days ago into about $ 990. Feels strange is that this $ 990 from the Silk Road coins account. For a while! Silk Road Bitcoin did not already under the control of the FBI (after the arrest of a black market)? Not only that, there are also other transfers account (stream? )。 It is a mystery!The NSA to be black is still a problem, we will continue to wait for the event to further ferment, tracking and reporting. But having said that, do you have any security at all in the world?Lei Feng network Note: writer Ouyang onions, FreeBuf hackers and geeks (FreeBuf.COM) authorizes the release of Lei Feng network (search for "Lei feng's network" public concerns), please indicate the source and author, no deletion of content.
Strange transactions per 0.001337 currencyAnd The Shadow is Brokers who probably many people curious. There's an interesting thing: reports from Security Affairs, two days before the Internet appeared a very strange deal, The Shadow Brokers accounts changed, a few days ago into about $ 990. Feels strange is that this $ 990 from the Silk Road coins account. For a while! Silk Road Bitcoin did not already under the control of the FBI (after the arrest of a black market)? Not only that, there are also other transfers account (stream? )。 It is a mystery!The NSA to be black is still a problem, we will continue to wait for the event to further ferment, tracking and reporting. But having said that, do you have any security at all in the world?Lei Feng network Note: writer Ouyang onions, FreeBuf hackers and geeks (FreeBuf.COM) authorizes the release of Lei Feng network (search for "Lei feng's network" public concerns), please indicate the source and author, no deletion of content.